M-Port: An AI-Powered DID Platform based on Biometric Information (II)
Why do we need DID?
DID can be the only bridge between users and platforms.
If we take a look at the history of the Internet, the way users create their digital identities is always changing. On Web 1.0, people create their digital identities through a combination of a user name and a password. On Web 2.0, people can still create an account through user name plus password, but they also have alternative ways of logging in that often require them to provide their real names, phone numbers, email addresses, or ID documents. The problem is doing so may compromise people’s data security.
A bigger concern is that users have no control over how their personal data is used, while Internet service providers, who don’t generate any of these data, get to profit from them. Not only do people have their personal data used by big tech companies for free, but also they are taken advantage of a second time when tech companies use such data for targeted push ads.
Therefore, although DID can serve as the bridge between users and Internet service providers, we need to find ways to create digital identities that are both secure and efficient, and achieving this requires no small number of technological innovations.
DID is the most valuable innovation made possible by Web 3.0.
Thanks to features such as immutability and hash encryption, decentralised identity (DID), a previously impossible way of creating digital identities has become available.

Different from centralised identities, DID gives control of personal information back to users, who will now be able to create unique digital identifiers for themselves through a trustable system. These identifiers can be verified through cryptological means such as digital signatures. This way, both users and Internet service providers get to benefit from more trustable and secure personal information usage and management solutions enabled by the blockchain.
Thanks to DID, users will truly own their personal data and get to decide how these data can be used. This is a huge step forward compared to relying on centralised Internet service providers. In fact, Ethereum, crypto wallets and other blockchain projects have already turned DID into a reality.
DID’s Structure and Challenges
In essence, DID is a string of address identifiers directly owned and controlled by users. Each identifier has a corresponding DID file that can be used to verify logins, encrypt messages, etc. Through password proofs (such as digital signatures), entities can prove their ownership of these identifiers. Individuals or entities may also approve these identifiers for use by others through encrypted proof methods (such as digital signatures). The structure of DID is illustrated below:
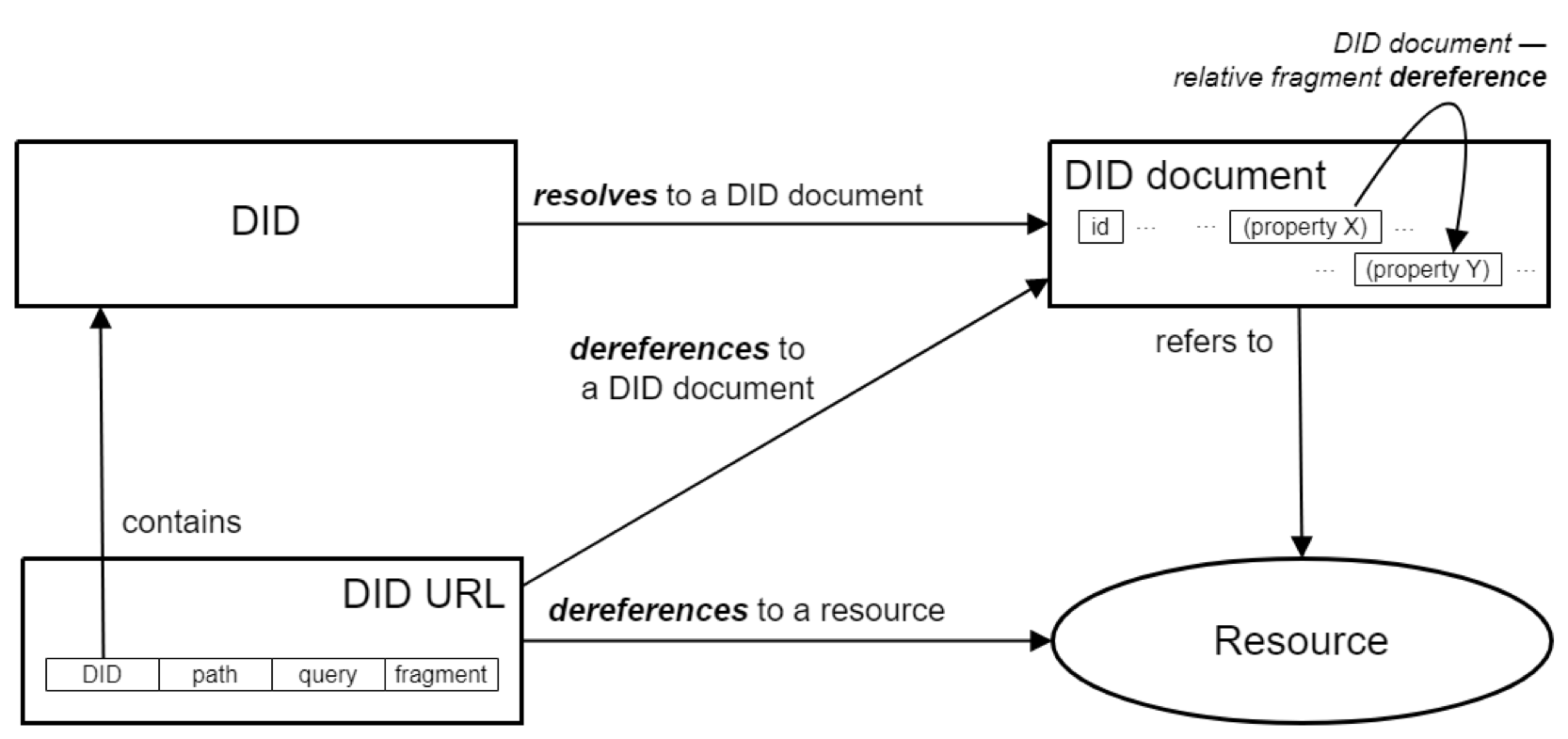
In a word, DID marks a breakup with traditional centralised Internet service providers and will hand back to people absolute control over their digital identities. This way, people get to decide when, under what conditions and with whom they disclose their personal information. At the same time, the blockchain only needs to verify users’ identities but doesn’t require them to provide any additional personal information. This arrangement makes for a higher level of privacy. As DID gets wider adoption, the barrier between different DID solutions will be broken, and people won’t be isolated in separate ecosystems.
Due to technological limitations as well as regulatory requirements, DID still faces many challenges.
For one thing, decentralisation, security and efficiency are mutually exclusive and impossible to be had all at the same time. Whether it’s blockchain, DID or Web 3.0, lots of innovations and breakthroughs still need to happen before we can make the blockchain efficient enough to serve our needs.
For another, although DID is all about linking real-world people with their virtual-world identities and guaranteeing anonymity while doing so, our current DeFi solutions are incapable of connecting addresses with real-world users. As a result, many economic activities that are commonplace in the real world won’t be possible in the virtual world, and an example of this would be borrowing when you don’t have enough collateral. For this reason, ordinary ways of identification such as photos or ID documents won’t be suitable for DID on Web 3.0, which creates yet another barrier to the wide adoption of DID.
Last updated